This kind of PLATYPUS is not a sweet and unusual mammal, this is a security problem recently announced that affects Intel across server, desktop and laptop CPUs. Along with a long list of other Intel issues that went public today (there's like 40 of them…), PLATYPUS is one that's gaining some attention and came with its own fancy website.
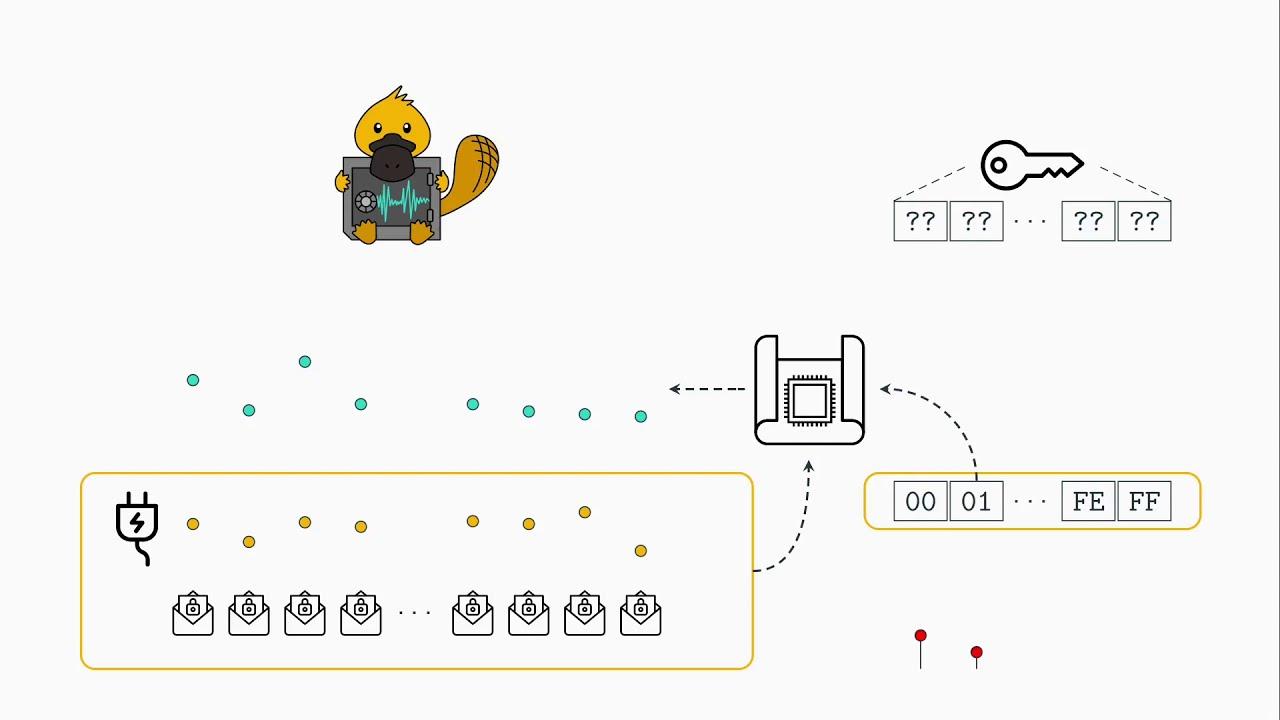
PLATYPUS (Power Leakage Attacks: Targeting Your Protected User Secrets) is a way to exploit the unprivileged access to the Intel RAPL (Running Average Power Limit) interface exposing the processor's power consumption to infer data and extract cryptographic keys. Physical access is not required the researchers say, so it's quite a concerning one.
You can check out these two videos they released to explain it a little:
Direct Link
Direct Link
Here's some more information from the website setup for PLATYPUS:
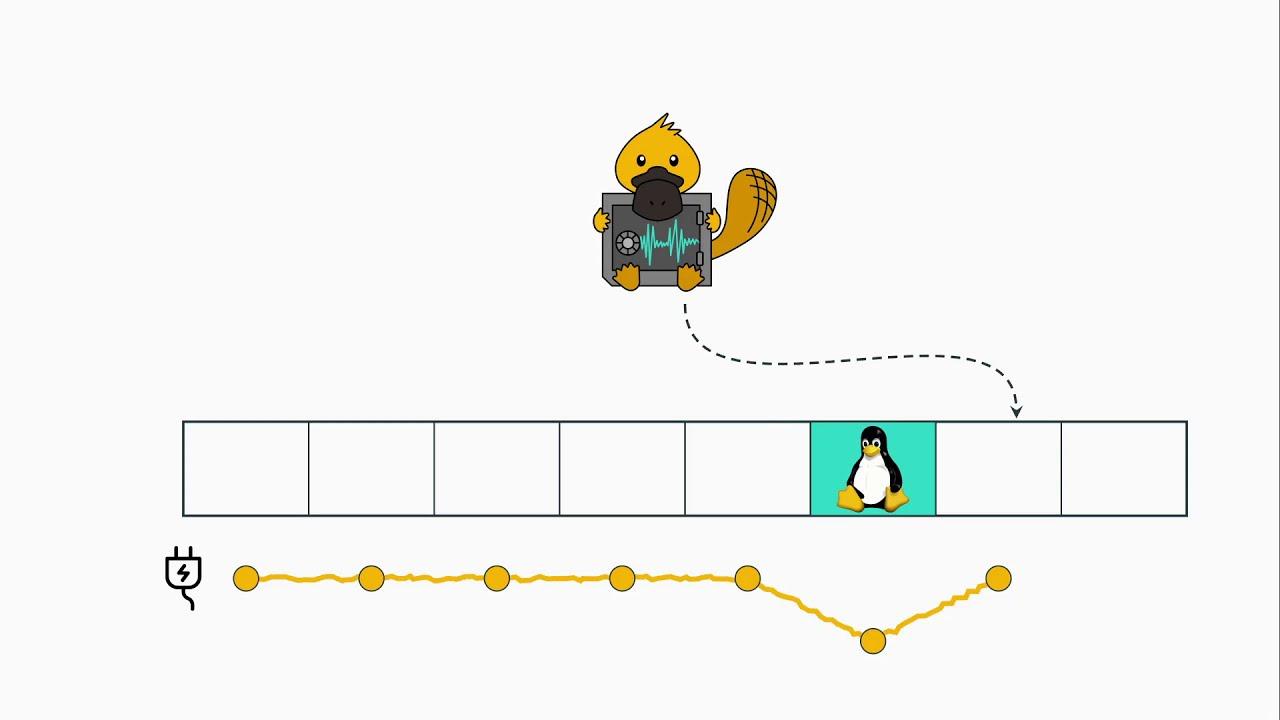
With classical power side-channel attacks, an attacker typically has physical access to a victim device. Using an oscilloscope, the attacker monitors the energy consumption of the device. With interfaces like Intel RAPL, physical access is not required anymore as the measurements can be accessed directly from software. Previous work already showed limited information leakage caused by the Intel RAPL interface. Mantel et al. showed that it is possible to distinguish if different cryptographic keys have been processed by the CPU. Paiva et al. established a covert channel by modulating the energy consumption of the DRAM.
Our research shows that the Intel RAPL interface can be exploited in way more threatening scenarios. We show that in addition to distinguishing different keys, it is possible to reconstruct entire cryptographic keys. We demonstrate this by recovering AES keys from the side-channel resilient AES-NI implementation, as well as RSA keys from an Intel SGX enclave. In addition, we distinguish different Hamming weights of operands or memory loads, threatening constant-time implementations of cryptographic algorithms. To mitigate PLATYPUS, the unprivileged access to the energy consumption has been revoked with an update to the operating system. With Intel SGX, however, a compromised operating system is within the threat model, rendering this mitigation insufficient. Therefore, Intel released microcode updates that change the way the energy consumption is reported if Intel SGX is enabled on the system. Instead of actual energy measurements, it falls back to a model-based approach, such that same instructions with different data or operands can not be distinguished.
Who is behind PLATYPUS? Various developers at Graz University of Technology, CISPA Helmholtz Center for Information Security and the University of Birmingham including: Moritz Lipp, Michael Schwarz, Andreas Kogler, David Oswald, Catherine Easdon, Claudio Canella and Daniel Gruss.
Are you directly affected? Well it goes all the way back to Sandy Bridge (2011), so have a look at the list of what's affected which can be found here. Intel released microcode updates to affected processors and for Linux there's been security updates to help with it. As always, ensure you're up to date everywhere possible.
The research does mention that other vendors are affected too like AMD from the Zen architecture onwards, but it appears limited to AMD Rome CPUs. ARM and NVIDIA too are possible as they all have these features available but the main testing has been done against Intel for now.
You can read more about PLATYPUS here. See the full Intel Security page for the rest of them.
Perry the Platypus, you did it again!
Where is Dr. Doofenschmitz when you need him?
Platypi are a myth, they have not be created yet.Turns out they're also [bioluminescent](https://www.livescience.com/platypuses-glow-uv-light.html).

Or, um, will be when they're created. Maybe the glow-in-the-dark thing is a byproduct of that production method.
Last edited by Purple Library Guy on 10 Nov 2020 at 9:55 pm UTC
Incidentally, the platypus was created by a number of woefully-overconfident wizards trying to teach the creator of the last continent how to paint.
Edit: Shit, sorry, keep forgetting this is roundworld. Don't mind me. Go about your business.
Last edited by WorMzy on 10 Nov 2020 at 10:11 pm UTC
Speaking of drifting off-topic... I saw a video a while back that was all about some of the ridiculous creatures in Dungeons and Dragons throughout the years....Turns out they're also [bioluminescent](https://www.livescience.com/platypuses-glow-uv-light.html).
Or, um, will be when they're created. Maybe the glow-in-the-dark thing is a byproduct of that production method.
I did not know that ! Thanks !
My apologies for drifting so much off-topic.
And now I want to see the specs for a Giant Platypus! I mean all other animals seem to have a 'Giant' version of them... Imagine riding one into battle?
But I don't see the Sandy Bridge CPU on that affected list.
It start with the 6th generation, am I wrong?
Last edited by Cyril on 11 Nov 2020 at 1:47 am UTC
Platypi are a myth, they have not be created yet.i'm laughing and its not just a little bit.

Giving names to vulnerabilities annoys me to no end.Right? Who started the damn trend? It is like naming nasty features of nature!
Speaking of drifting off-topic... I saw a video a while back that was all about some of the ridiculous creatures in Dungeons and Dragons throughout the years....Platypuses are like real-world Owlbears, except they're Duckbeavers.
And now I want to see the specs for a Giant Platypus! I mean all other animals seem to have a 'Giant' version of them... Imagine riding one into battle?
Last edited by Nanobang on 11 Nov 2020 at 12:27 pm UTC
You know who has a [platypus mascot](http://www.hexley.com/)? [The Darwin project](https://developer.apple.com/library/archive/referencelibrary/GettingStarted/GS_Darwin/_index.html#//apple_ref/doc/uid/TP30001006), of course...
... and yesterday, Apple released their first arm-based line.
COINCIDENCE? I think not...
Ah shit, here we go again...
But I don't see the Sandy Bridge CPU on that affected list.
It start with the 6th generation, am I wrong?
It starts with Sandy Bridge. But that generation had AES-NI instructions only for I5 or above.
https://en.wikipedia.org/wiki/AES_instruction_set
OK, thanks, still confusing I think, why not listing properly the affected CPU then?
Owlbears don't have bio luminescence though! The platypus really is a 'god was bored' creature.Speaking of drifting off-topic... I saw a video a while back that was all about some of the ridiculous creatures in Dungeons and Dragons throughout the years....Platypuses are like real-world Owlbears, except they're Duckbeavers.
And now I want to see the specs for a Giant Platypus! I mean all other animals seem to have a 'Giant' version of them... Imagine riding one into battle?
I think as a game master I'm going to make Owlbears have bioluminescence from now on.Owlbears don't have bio luminescence though! The platypus really is a 'god was bored' creature.Speaking of drifting off-topic... I saw a video a while back that was all about some of the ridiculous creatures in Dungeons and Dragons throughout the years....Platypuses are like real-world Owlbears, except they're Duckbeavers.
And now I want to see the specs for a Giant Platypus! I mean all other animals seem to have a 'Giant' version of them... Imagine riding one into battle?








 10 Nov 2020
10 Nov 2020



 How to set, change and reset your SteamOS / Steam Deck desktop sudo password
How to set, change and reset your SteamOS / Steam Deck desktop sudo password How to set up Decky Loader on Steam Deck / SteamOS for easy plugins
How to set up Decky Loader on Steam Deck / SteamOS for easy plugins
See more from me